When working in a Linux system, navigating through files and directories is a common task. To access a file or directory, you need to specify…
Understanding the file system hierarchy in a Linux system is crucial for navigating and managing files effectively. The Linux file system follows the Filesystem Hierarchy…
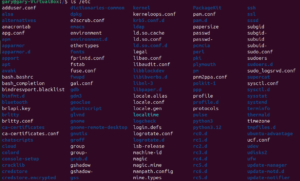
The Linux command line is a versatile tool that provides powerful ways to manage files, execute programs, and control the system. Understanding basic commands and…
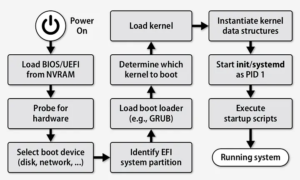
The Linux boot and startup processes are complex and involve several stages. Here’s a detailed overview of how they work: 1. BIOS/UEFI Initialization When a…
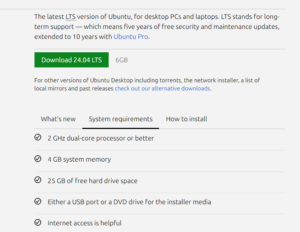
Installing Ubuntu in VirtualBox involves several steps. Here’s a detailed guide to help you through the process: System Requirement for Ubuntu Desktop 24.04 LTS…
What is VirtualBox? Virtual Machine abstracts the hardware of our personal computers such as CPU, disk drives, memory, NIC (Network Interface Card), etc, into many…
Linux distributions, often referred to as “distros,” are operating systems based on the Linux kernel. They bundle together the Linux kernel with a collection of…
Linux and Unix are closely related operating systems, but they have distinct differences in terms of their development, usage, and features. Here’s a detailed comparison…
Linux and Windows are two of the most widely used operating systems (OS), each with its own set of features, benefits, and drawbacks. Here’s a…
Linux differs from other operating systems in several key ways, ranging from its open-source nature and licensing to its architecture, flexibility, and community-driven development model.…
The history of the Linux operating system is a fascinating journey from a personal project by a student to a global, open-source powerhouse. Here’s an…
What is Operating System ? An operating system (OS) is software that manages the hardware and software resources of a computer system, providing a foundation…
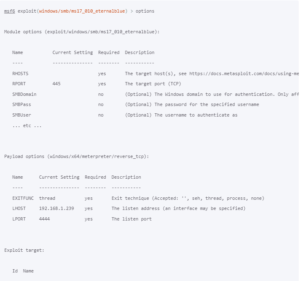
What is Metasploit Framework? The Metasploit Framework is a powerful open-source tool used by cybersecurity professionals and ethical hackers to conduct penetration testing, identify security…
Remote access in ethical hacking refers to the methods and tools used by penetration testers (ethical hackers) to access systems and networks remotely to identify…
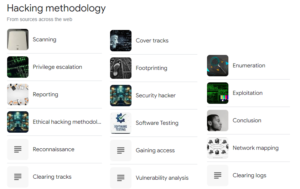
The methodology followed by hackers, particularly those involved in malicious activities, typically involves a series of systematic steps designed to breach security defenses, exploit vulnerabilities,…
Hacktivism is a form of activism that leverages hacking techniques to promote political, social, or ideological agendas. It combines “hacking” and “activism,” reflecting the use…
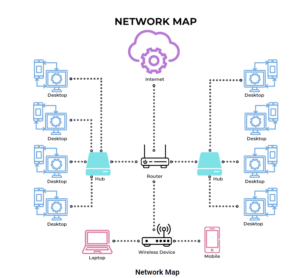
Network mapping can be done using a combination of manual methods and automated tools. Here’s a step-by-step guide to performing network mapping: 1. Define Your…
Keyword search intent (also known as user intent or search intent) refers to the purpose or goal behind a user’s search query. Understanding search intent…
Keyword research is a fundamental part of SEO, helping you identify the search terms that your target audience uses to find information, products, or services.…
In the context of SEO (Search Engine Optimization), ranking refers to the position of a webpage in the search engine results pages (SERPs) for a…