Network mapping is the process of discovering and visualizing the physical and logical components of a network. This involves identifying the various devices, such as computers, routers, switches, firewalls, and servers, as well as understanding how these devices are connected and interact with each other. The goal of network mapping is to create a comprehensive diagram or map that provides an overview of the network’s structure and connectivity.
Here are some key aspects of network mapping:
- Discovery: Network mapping starts with the discovery phase, where tools scan the network to identify all connected devices and their attributes. This can include IP addresses, MAC addresses, hostnames, operating systems, and open ports.
- Topology Visualization: Once the devices are discovered, network mapping tools create visual representations of the network topology. These maps illustrate how devices are interconnected and can highlight the network’s physical layout (cabling, devices locations) or its logical layout (network segments, VLANs, subnets).
- Device Information: Network maps often include detailed information about each device, such as configuration settings, software versions, and performance metrics. This can help in managing and troubleshooting the network.
- Path Analysis: Some network mapping tools provide path analysis features, which show the data flow between devices, helping to identify bottlenecks or potential points of failure.
- Monitoring and Alerts: Advanced network mapping tools offer real-time monitoring capabilities, alerting administrators to changes in the network topology or performance issues. This proactive approach can help in maintaining network health and security.
- Security Assessment: By providing a clear view of the network, mapping tools can help identify vulnerabilities, unauthorized devices, and potential attack paths, aiding in the overall security posture of the network.
- Documentation and Compliance: Network maps serve as important documentation for IT teams, aiding in network planning, troubleshooting, and audits. They can also help in meeting compliance requirements by providing clear records of the network structure and its security measures.
Common tools used for network mapping include:
- Nmap: A popular open-source tool used for network discovery and security auditing.
- SolarWinds Network Topology Mapper: A comprehensive tool that provides detailed network maps and monitoring features.
- Microsoft Visio: Often used for creating manual network diagrams, although it requires manual input and maintenance.
- Nagios XI: Offers network monitoring and can visualize network topologies.
- Cisco Network Assistant: A tool for managing and mapping Cisco network devices.
In summary, network mapping is a crucial activity for network management, providing insights into the network’s layout, performance, and security, thereby enabling effective administration and troubleshooting.
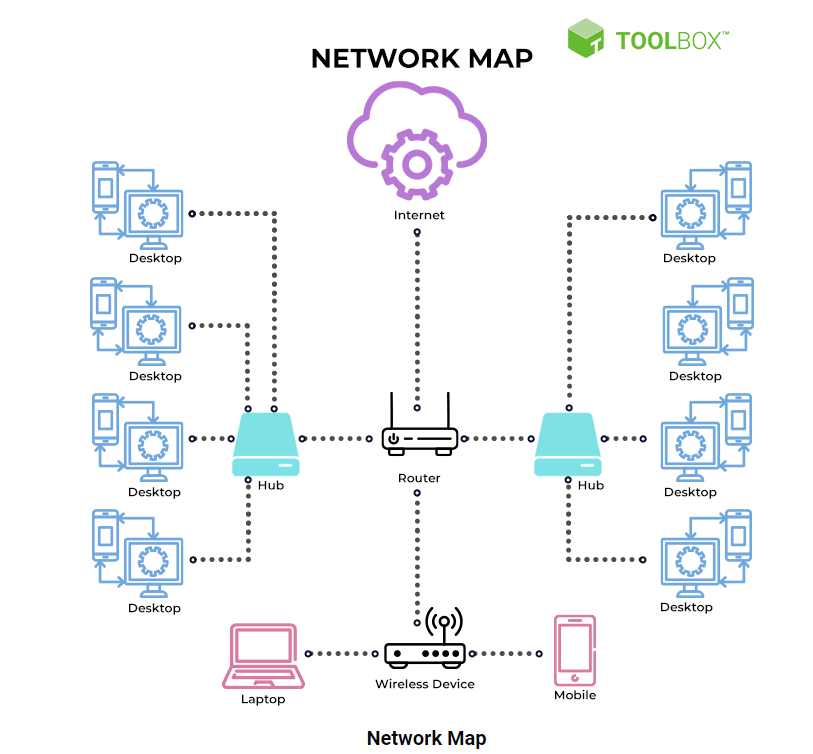
How Does Network Mapping Work?
Network mapping is the process of discovering and visualizing the components, connections, and structure of a computer network. It involves several steps, including data collection, analysis, and visualization, to create a comprehensive map of the network. Here’s an overview of how network mapping works:
1. Data collection: The first step in network mapping is gathering information about the devices, components, and connections within the network. This can be achieved using various methods, such as:
- Network scanning: Network scanners, like Nmap or Zenmap, can actively probe devices on the network to identify their IP addresses, open ports, and running services.
- SNMP: Simple Network Management Protocol (SNMP) is a widely-used protocol that allows network devices to share information about their status, configuration, and performance with network management systems.
- Network monitoring tools: Tools like SolarWinds Network Performance Monitor, PRTG, or Zabbix can passively collect data about the devices and connections in the network by monitoring traffic, analyzing logs, or querying device configuration databases
2. Data analysis: Once the data is collected, it needs to be analyzed to identify the devices, their roles, and the relationships between them. This step may involve:
- Device identification: Determining the type of each device (e.g., router, switch, server, workstation) and its function within the network.
- Connection mapping: Establishing the connections between devices, including their physical links (e.g., Ethernet, fiber, Wi-Fi) and logical relationships (e.g., subnets, routing paths, VLANs).
- Network metrics: Calculating network performance metrics, such as latency, throughput, and packet loss, which help to identify potential bottlenecks or issues in the network.
3. Visualization: The final step in network mapping is creating a visual representation of the network’s structure, connections, and components. Visualization tools, such as Microsoft Visio, Lucidchart or specialized network mapping software like SolarWinds Network Topology Mapper, can be used to generate network maps in various formats, including:
- Physical topology: This type of map displays the physical layout of network devices and the connections between them, providing insights into the network’s infrastructure and potential physical limitations.
- Logical topology: This map focuses on the logical relationships between devices, such as IP addressing schemes, routing paths, and VLANs, revealing the flow of data within the network.