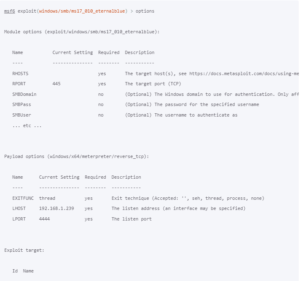
What is Metasploit Framework? The Metasploit Framework is a powerful open-source tool used by cybersecurity professionals and ethical hackers to conduct penetration testing, identify security…
Remote access in ethical hacking refers to the methods and tools used by penetration testers (ethical hackers) to access systems and networks remotely to identify…
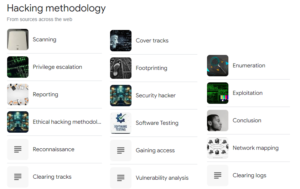
The methodology followed by hackers, particularly those involved in malicious activities, typically involves a series of systematic steps designed to breach security defenses, exploit vulnerabilities,…
Hacktivism is a form of activism that leverages hacking techniques to promote political, social, or ideological agendas. It combines “hacking” and “activism,” reflecting the use…
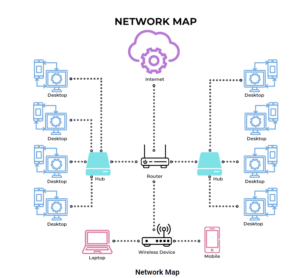
Network mapping can be done using a combination of manual methods and automated tools. Here’s a step-by-step guide to performing network mapping: 1. Define Your…
Mitigating a Distributed Denial of Service (DDoS) attack involves implementing various strategies and deploying specialized tools to minimize the impact and restore normal operation. The…
a bandwidth attack aims to overwhelm a network by saturating it with an excessive amount of data, causing the available bandwidth to be fully utilized…
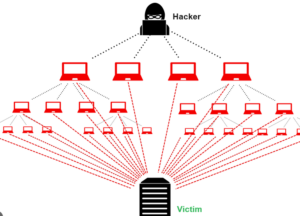
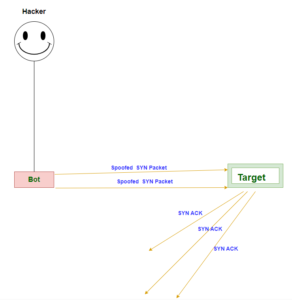
A Distributed Denial of Service (DDoS) attack is a malicious attempt to disrupt the regular functioning of a network, service, or website by overwhelming it…
An Ethical Hacking tutorial typically refers to educational content that provides guidance and instruction on ethical hacking or penetration testing. Ethical hacking involves authorized and…