End-to-end encryption (E2EE) is a method of implementing a secure communication system where only communicating users can participate. No one else, including the system provider, telecom providers, Internet providers or malicious actors, can access the cryptographic keys needed to read or send messages.
End-to-end encryption prevents data from being read or secretly modified, except by the true sender and intended recipients. Frequently, the messages are relayed from the sender to the recipients by a service provider. However, messages are encrypted by the sender and no third party, including the service provider, has the means to decrypt them. The recipients retrieve the encrypted messages and decrypt them independently. Since third parties cannot decrypt the data being communicated or stored, services that provide end-to-end encryption are better at protecting user data when they are affected by data breaches. Such services are also unable to share user data with government authorities, domestic or international.
In 2022, the UK’s Information Commissioner’s Office, the government body responsible for enforcing online data standards, stated that opposition to E2EE was misinformed and the debate too unbalanced, with too little focus on benefits, since E2EE helped keep children safe online and law enforcement access to stored data on servers was “not the only way” to find abusers.
End-to-end encryption (E2EE) is a security method that ensures only the intended sender and recipient(s) of a message can read its content. The data is encrypted on the sender’s device and can only be decrypted by the recipient on their device. No third party, including service providers, internet intermediaries, or hackers, can access or decipher the information while it’s in transit or stored.
How Does E2EE Work ?
- Encryption on the Sender’s Side:
- Data (e.g., a message, email, or file) is encrypted on the sender’s device using the recipient’s public encryption key.
- Data Transmission:
- The encrypted data travels through servers or networks in an unreadable format. If intercepted, it appears as scrambled text.
- Decryption on the Recipient’s Side:
- Only the recipient, using their private decryption key, can decrypt and access the original data.
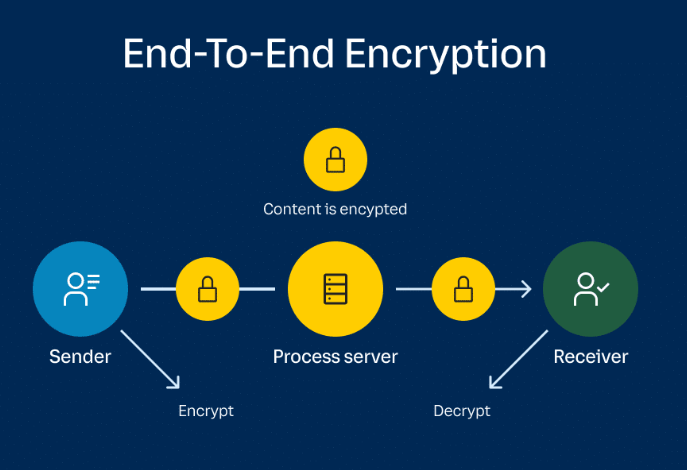
End-to-end encryption is a relatively straightforward process that involves transforming readable data into an unreadable format, transmitting it securely and converting it back into its original form at the destination.
Specifically, E2EE generally includes these four steps:
- Encryption
- Transmission
- Decryption
- Authentication
1. Encryption
E2EE begins by using an encryption algorithm to encrypt the sensitive data. This algorithm uses complex mathematical functions to scramble the data into an unreadable format, known as ciphertext. Only authorized users with a secret key, known as the decryption key, can read the messages.
E2EE can use an asymmetric encryption scheme, which uses two different keys to encrypt and decrypt data, or a symmetric encryption scheme, which uses a single shared key for encryption and decryption. Many E2EE implementations use a combination of the two (see “Symmetric versus asymmetric encryption”).
2. Transmission
Encrypted data (ciphertext) travels over a communication channel such as the internet or other networks. The message remains unreadable to application servers, internet service providers (ISPs), hackers or other entities as it moves to its destination. Instead, it appears as random, unintelligible characters to anyone who might intercept it.
3. Decryption
Upon reaching the recipient’s device, ciphertext gets decrypted using the recipient’s private key (in asymmetric encryption) or the shared key (in symmetric encryption). Only the recipient possesses the private key necessary to decrypt the data.
4. Authentication
Decrypted data is verified to ensure its integrity and authenticity. This step might involve verifying the sender’s digital signature or other credentials to confirm that no one tampered with the data during transmission.
What Kind of Encryption Does E2EE Use?
End-to-end encryption (E2EE) typically relies on asymmetric encryption combined with symmetric encryption to ensure secure communication. Here’s an overview of the encryption techniques used in E2EE:
1. Asymmetric Encryption (Public-Private Key Cryptography)
- What It Is: A cryptographic system that uses two keys:
- A public key, shared with others to encrypt messages.
- A private key, kept secret and used to decrypt messages.
- How It Works in E2EE:
- The sender encrypts a message using the recipient’s public key.
- The recipient decrypts the message using their private key.
- Algorithms Commonly Used:
- RSA (Rivest-Shamir-Adleman): Widely used but slower than modern alternatives.
- Elliptic Curve Cryptography (ECC): Faster and more secure with smaller key sizes.
- Popular ECC variants include Curve25519 and P-256.
2. Symmetric Encryption
- What It Is: A cryptographic system where the same key is used for both encryption and decryption.
- How It Works in E2EE:
- Symmetric encryption is often used for encrypting the actual message (bulk data).
- A randomly generated symmetric key (called a session key) encrypts the content.
- This session key is encrypted using the recipient’s public key (asymmetric encryption).
- Algorithms Commonly Used:
- AES (Advanced Encryption Standard): A fast and secure block cipher, often used with 128-bit, 192-bit, or 256-bit keys.
3. Key Exchange Protocols
- E2EE also uses secure key exchange protocols to establish encryption keys between the sender and recipient without exposure to third parties.
- Common Protocols:
- Diffie-Hellman (DH) and Elliptic Curve Diffie-Hellman (ECDH): Securely exchange keys over an untrusted network.
- Signal Protocol: Used in apps like Signal, WhatsApp, and Skype, combining X3DH (Extended Triple Diffie-Hellman) with other cryptographic techniques.
4. Message Authentication (Optional but Common)
- Ensures that messages are not tampered with during transmission and verifies the sender’s identity.
- Algorithms Used:
- HMAC (Hash-Based Message Authentication Code): Often paired with symmetric encryption.
- Digital Signatures: Created using the sender’s private key and verified with their public key.
Why Combine Asymmetric and Symmetric Encryption?
- Asymmetric encryption is computationally expensive and best suited for small amounts of data (e.g., session keys).
- Symmetric encryption is faster and better for encrypting large amounts of data (e.g., email or chat messages).
By combining both methods, E2EE achieves robust security and efficiency.
Benefits of E2EE Email
Using an end-to-end encryption (E2EE) email service offers several benefits, particularly for users who prioritize privacy, security, and confidentiality. Here’s a detailed breakdown:
1. Privacy Protection
- Service Providers Can’t Access Content: Even the email provider cannot read your emails because they don’t hold the decryption keys.
- Shield from Advertisers: Unlike many free email providers that scan emails for ad targeting (e.g., Gmail), E2EE services ensure your content remains private.
- No Data Harvesting: Your emails are not analyzed, mined, or shared for marketing or analytics purposes.
2. Enhanced Security
- Protection Against Hackers: Emails remain encrypted during transmission and storage, so even if someone intercepts them, they can’t read the content.
- Data Integrity: Encryption ensures that your messages cannot be tampered with during transit.
- Resilience Against Server Breaches: If the email provider’s servers are hacked, encrypted emails remain unreadable without the recipient’s private key.
3. Compliance with Privacy Laws
- Meets Regulations: Using E2EE email services helps organizations comply with strict data protection laws like GDPR (Europe), HIPAA (USA), or CCPA (California).
- Safeguards Sensitive Data: Essential for industries like healthcare, legal, and finance, where confidentiality is mandatory.
4. Secure Communication in Sensitive Situations
- Ideal for journalists, whistleblowers, activists, and anyone communicating in high-risk situations, as it protects against surveillance and censorship.
- Offers anonymous accounts on some platforms, making it harder to link emails back to your identity.
5. Prevents Man-in-the-Middle Attacks
- Emails are encrypted on the sender’s device and decrypted on the recipient’s device, ensuring that no intermediaries (e.g., internet providers, governments, or bad actors) can intercept and read your messages.
6. Cross-Device Security
- With E2EE, the security of your emails is maintained across all devices, ensuring that your communications are safe even on mobile phones or public networks.
7. Builds Trust
- If you are a professional or business, using E2EE email shows clients and partners that you prioritize privacy and take their data seriously.
8. Unaffected by Subpoenas
- Because E2EE email providers cannot decrypt your emails, they cannot share your messages with governments, even if legally compelled.
9. Long-Term Confidentiality
- Even if someone gains access to an encrypted email years later, they cannot decrypt it without the appropriate keys. This ensures that sensitive historical communications remain safe.
10. Optional Anonymity
- Many E2EE providers, like ProtonMail or Tutanota, allow users to sign up without personal information, ensuring a higher level of anonymity.
11. No Reliance on Trust
- With E2EE, you don’t need to trust the service provider because encryption is mathematically secure, not reliant on company policies or promises.
12. Protects Against Future Threats
- Forward Secrecy: Many E2EE services use cryptographic techniques that protect your data even if encryption keys are compromised in the future.
- Helps safeguard against the potential threats of quantum computing with evolving encryption standards.
Where Is E2EE Used ?
End-to-end encryption (E2EE) is used in various applications and services to protect sensitive data and ensure privacy. Here are the main areas where E2EE is commonly implemented:
1. Messaging Applications
E2EE Messaging Application Listing
E2EE is widely used in messaging platforms to secure conversations between users.
- Examples:
- Signal: Known for strong E2EE, protecting texts, voice calls, and video calls.
- WhatsApp: Uses E2EE for all messages and calls (based on the Signal protocol).
- iMessage: Apple’s messaging app encrypts messages sent between Apple devices.
- Telegram (Secret Chats): Offers optional E2EE for one-on-one “secret” chats.
- Viber: Provides E2EE for texts, calls, and media.
2. Email Services
Secure email providers use E2EE to ensure that only the sender and recipient can read the content of emails.
The E2EE Email Provider Listing
- Examples:
- ProtonMail: Automatically encrypts emails end-to-end for ProtonMail users.
- Tutanota: Offers E2EE for emails, including subject lines and attachments.
- Mailfence: Provides encrypted email and digital signatures.
- Posteo: A privacy-focused email service with optional E2EE.
3. File Storage and Sharing
E2EE is used to encrypt files, ensuring that only authorized users can access them.
- Examples:
- Tresorit: A secure cloud storage service with E2EE.
- Sync.com: Provides zero-knowledge, E2EE file storage and sharing.
- pCloud (Crypto): Offers an optional E2EE add-on for secure file storage.
- Mega: Uses E2EE for file uploads and downloads.
4. Video and Voice Communication
E2EE ensures that calls and video meetings remain private, with no access by third parties or service providers.
- Examples:
5. Secure Collaboration Tools
Some collaboration platforms implement E2EE for sensitive communications and file sharing.
- Examples:
- Element (Matrix Protocol): A decentralized collaboration tool with E2EE for chats and file sharing.
- Wire: A secure messaging platform for teams with E2EE.
- CryptPad: Provides E2EE for collaborative document editing.
6. Cryptocurrency and Blockchain Platforms
Cryptographic principles in E2EE are also fundamental in cryptocurrency wallets and blockchain-based systems to secure user data and transactions.
- Examples:
- Cryptocurrency Wallets: Hardware wallets (e.g., Ledger, Trezor) and software wallets (e.g., MetaMask) rely on encryption to protect private keys.
- Blockchain Messaging Apps: Platforms like Status use E2EE for messaging.
7. Password Managers
E2EE is essential in password managers to secure user credentials.
- Examples:
- 1Password
- LastPass
- Bitwarden
- Dashlane
8. Browsers and Search Engines
While E2EE is not directly applied to browsing itself, secure search engines and tools protect user queries and traffic.
- Examples:
- Tor Browser: Ensures anonymity and encryption for browsing.
- DuckDuckGo: Provides encrypted search results and private browsing features.
9. IoT (Internet of Things) Devices
E2EE is being increasingly adopted to secure communications between IoT devices, protecting data from unauthorized access.
- Examples:
- Smart home systems like Apple HomeKit.
- Security cameras with encrypted streams.
10. Healthcare and Legal Industries
Sensitive communications in healthcare and legal fields are often protected by E2EE to comply with privacy regulations like HIPAA.
- Examples:
- Encrypted patient portals.
- Secure document-sharing platforms for lawyers.
11. Secure Web Browsing
While traditional HTTPS encrypts communication between the browser and server, some platforms aim to extend E2EE principles to web applications.
- Examples:
- Secure web apps like Proton Drive.
- Decentralized applications (dApps) built on Web3 technologies.
12. Activism and Whistleblowing Platforms
E2EE ensures anonymity and safety for individuals communicating in oppressive or high-risk environments.
- Examples:
- SecureDrop: A platform for whistleblowers to securely submit documents.
- Tor Project: Helps activists and journalists communicate securely.