Anycast is a network addressing and routing methodology used in computer networks to provide a single destination address for multiple servers. In the context of…
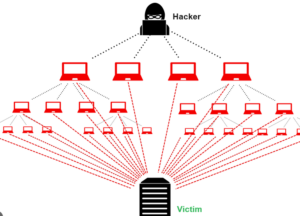
A Distributed Denial of Service (DDoS) attack is a malicious attempt to disrupt the regular functioning of a network, service, or website by overwhelming it…
Ethical hacking, also known as penetration testing or white-hat hacking, is the practice of intentionally probing systems, networks, or applications to identify and fix security…
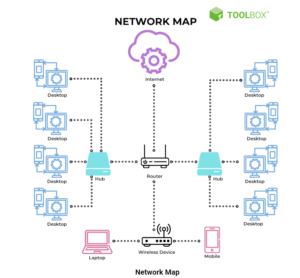
Network mapping is the process of discovering and visualizing the physical and logical components of a network. This involves identifying the various devices, such as…
Nikto is a widely-used open-source web server scanner that performs comprehensive tests against web servers to detect vulnerabilities, misconfigurations, and other security issues. It is…
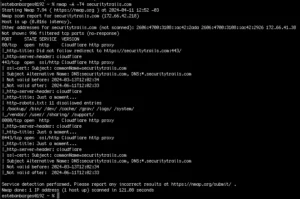
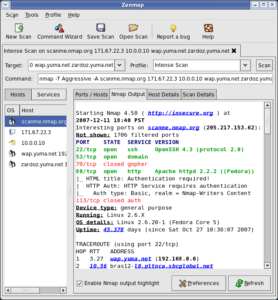
Nmap (“Network Mapper”) is a free and open source utility for network discovery and security auditing. Many systems and network administrators also find it useful for tasks…
Termux is a versatile and powerful terminal emulator and Linux environment app for Android. It allows users to run a Linux distribution alongside their Android…
Vulnerability scanning is a process used to identify security weaknesses and potential vulnerabilities in computer systems, networks, applications, and devices. It involves using automated tools…