a bandwidth attack aims to overwhelm a network by saturating it with an excessive amount of data, causing the available bandwidth to be fully utilized and leading to network congestion or, in some cases, a complete denial of service.
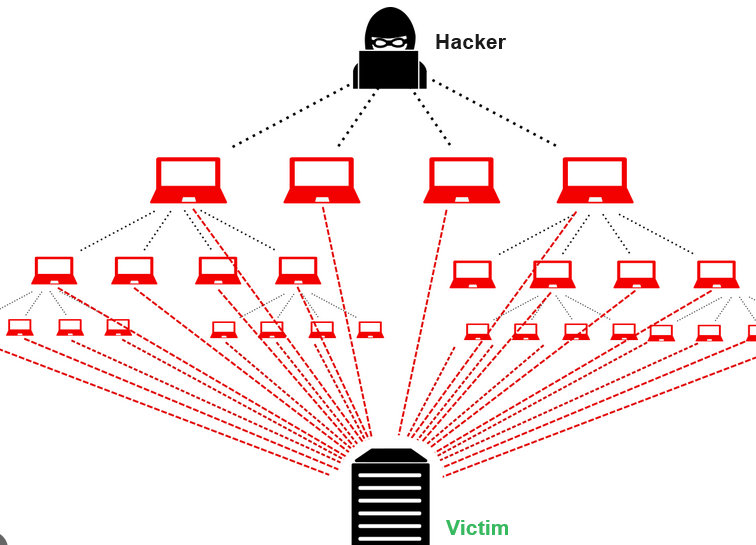
The method involves sending a high volume of packets to the target computer or server, pushing its processing power and memory to the limit. Once the system’s capacity is reached, it becomes challenging for it to handle legitimate traffic, resulting in degraded performance or a loss of service.
As mentioned, these attacks can be carried out manually using tools like NetFlows, or they can be automated through the use of botnets controlled by malicious actors. Mitigating such attacks typically involves implementing network security measures, traffic monitoring, and employing tools that can identify and block malicious traffic to prevent bandwidth saturation.
Volumetric Attacks
A volumetric attack is a type of cyber attack that focuses on overwhelming a target’s network, system, or online service by flooding it with a massive volume of traffic. The goal of a volumetric attack is to consume the available bandwidth, exhaust computing resources, and disrupt the normal functioning of the target. These attacks fall under the broader category of Distributed Denial of Service (DDoS) attacks.
Key characteristics of volumetric attacks include:
- High Volume of Traffic: Volumetric attacks generate an enormous amount of traffic with the intent of saturating the target’s network infrastructure.
- Network Congestion: The overwhelming volume of incoming data leads to network congestion, making it challenging for legitimate users to access the targeted resources.
- Bandwidth Exhaustion: The attack aims to consume the entire bandwidth of the target, leaving limited or no capacity for regular traffic.
- Botnets: Volumetric attacks are often carried out using botnets, which are networks of compromised computers controlled by a single entity.
- Amplification Techniques: Attackers may leverage amplification techniques, such as DNS amplification or NTP amplification, to magnify the volume of attack traffic.
- UDP Floods: Utilizing User Datagram Protocol (UDP) packets, attackers flood the target with a large number of requests, contributing to the volumetric nature of the attack.
Volumetric attacks can have severe consequences, leading to service outages, downtime, and financial losses for the targeted organization. Mitigation strategies against volumetric attacks typically involve using specialized DDoS protection services, traffic filtering, and implementing rate limiting to manage and mitigate the impact of the massive influx of traffic.
Bandwidth Flood Attacks
A “Bandwidth Flood Attack” refers to a type of cyber attack where the primary objective is to inundate a target network or system with an overwhelming amount of traffic, with the specific aim of exhausting the available bandwidth. This type of attack falls under the broader category of volumetric DDoS attacks.
Key characteristics of a bandwidth flood attack include:
- Excessive Traffic: The attacker generates an abnormally high volume of network traffic, intending to consume the entire bandwidth capacity of the target.
- Network Saturation: The goal is to saturate the target’s network infrastructure, causing congestion and making it difficult for legitimate users to access services or resources.
- Resource Exhaustion: As the network becomes saturated, computing resources, such as routers, switches, and servers, may become overwhelmed and unable to process the sheer volume of incoming data.
- Botnet Utilization: Bandwidth flood attacks are often executed using a botnet, which is a network of compromised computers controlled by the attacker. These bots collectively contribute to the flood of traffic.
- Distributed Nature: In some cases, the attack may be distributed, involving multiple sources to make it harder to trace and mitigate.