A Distributed Denial of Service (DDoS) attack is a malicious attempt to disrupt the regular functioning of a network, service, or website by overwhelming it with a flood of internet traffic.
A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic.
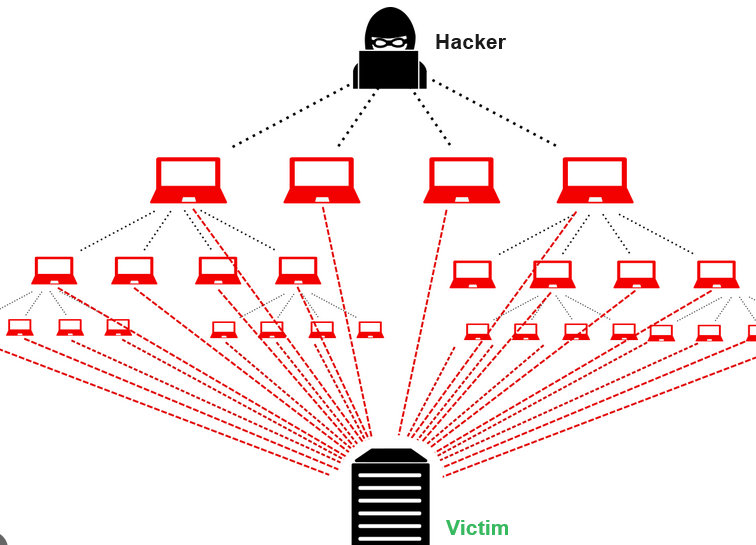
DDoS attacks achieve effectiveness by utilizing multiple compromised computer systems as sources of attack traffic. Exploited machines can include computers and other networked resources such as IoT devices.
From a high level, a DDoS attack is like an unexpected traffic jam clogging up the highway, preventing regular traffic from arriving at its destination.
In a DDoS attack, the targeted system or network is bombarded with a massive volume of requests or data, making it difficult or impossible for legitimate users to access the service.
Here are key characteristics and components of a DDoS attack:
- Distributed Nature: DDoS attacks involve multiple sources, often using a network of compromised computers (botnets) to generate and direct traffic toward the target. This distributed nature makes it challenging to mitigate the attack by blocking a single source.
- Volume of Traffic: DDoS attacks aim to flood the target with an excessive amount of traffic, overwhelming its capacity to handle legitimate requests. This can lead to degraded performance or complete unavailability of the targeted service.
- Variety of Attack Vectors: DDoS attacks can take various forms and use different techniques to disrupt services. Common attack vectors include UDP reflection, SYN/ACK flooding, DNS amplification, and HTTP flooding.
- Motivations: DDoS attacks can be motivated by various factors, including ideological reasons, revenge, competitive rivalry, or extortion attempts. Hacktivist groups, criminals, and individuals may use DDoS attacks as a means to achieve their goals.
- Impact: The impact of a successful DDoS attack can be severe, resulting in downtime, financial losses, damage to reputation, and potential data breaches. The goal is to render the targeted system or network unavailable to its intended users.
- Mitigation: Organizations employ various DDoS mitigation strategies and solutions to detect and filter malicious traffic during an attack. These may include traffic filtering devices, load balancers, and content delivery networks (CDNs) that can absorb and distribute the incoming traffic.
- Reflection and Amplification: Some DDoS attacks use reflection and amplification techniques, where attackers exploit misconfigured servers or devices to bounce and amplify their traffic. This makes it challenging to trace the source and increases the effectiveness of the attack.
- Legitimate-Looking Requests: Attackers may attempt to make their traffic appear legitimate, making it harder for traditional security measures to distinguish between malicious and legitimate requests.
It’s important for organizations to have DDoS mitigation strategies in place to detect and mitigate these attacks.
How Does a DDoS Attack Work?

DDoS attacks are carried out with networks of Internet-connected machines.
These networks consist of computers and other devices (such as IoT devices)which have been infected with malware, allowing them to be controlled remotely by an attacker. These individual devices are referred to as bots (or zombies), and a group of bots is called a botnet.
Once a botnet has been established, the attacker is able to direct an attack by sending remote instructions to each bot.
When a victim’s server or network is targeted by the botnet, each bot sends requests to the target’s IP address, potentially causing the server or network to become overwhelmed, resulting in a denial-of-service to normal traffic.
Because each bot is a legitimate Internet device, separating the attack traffic from normal traffic can be difficult.
DDoS attacks are characterized by their distributed nature, involving multiple sources that coordinate to flood the target. Here’s a general overview of how a DDoS attack works:
- Recruitment of Botnets:
- Attackers often control a network of compromised computers, known as a botnet. These compromised devices may include computers, servers, Internet of Things (IoT) devices, and other connected devices.
- Botnets can be created through malware infections, exploiting vulnerabilities, or using other illicit means to gain control over the devices.
- Coordination and Control:
- The attacker uses a command and control (C&C) infrastructure to coordinate the activities of the botnet. This infrastructure allows the attacker to send instructions to the compromised devices within the botnet.
- Initiation of the Attack:
- The attacker initiates the DDoS attack by directing the botnet to send a massive volume of traffic to the target. This flood of traffic is designed to overwhelm the target’s resources, such as bandwidth, processing power, or memory.
- Attack Vectors:
- DDoS attacks can use various attack vectors or techniques to achieve their goals. Common attack vectors include:
- UDP Reflection: Exploiting servers that respond to UDP (User Datagram Protocol) requests with larger responses than the initial requests, amplifying the volume of traffic.
- SYN/ACK Floods: Overwhelming the target with a flood of TCP (Transmission Control Protocol) connection requests, exhausting resources.
- DNS Amplification: Exploiting misconfigured DNS servers to amplify the size of the response sent to the target.
- HTTP/S Floods: Sending a large number of HTTP/S requests to exhaust the target’s web server resources.
- DDoS attacks can use various attack vectors or techniques to achieve their goals. Common attack vectors include:
- Detection and Mitigation:
- The targeted organization or service provider employs various tools and strategies to detect and mitigate the DDoS attack. This may include traffic filtering devices, intrusion prevention systems (IPS), and DDoS mitigation services.
- Some organizations use content delivery networks (CDNs) to distribute and absorb traffic, helping to mitigate the impact of an attack.
- Impact on the Target:
- The sustained and overwhelming volume of traffic leads to a degradation of service or complete unavailability. Legitimate users may experience slow loading times, timeouts, or inability to access the targeted service.
- Duration and Persistence:
- DDoS attacks can be short-lived or prolonged, depending on the attacker’s goals. Some attacks may be used as a distraction tactic, diverting attention from other malicious activities.
- Post-Attack Analysis:
- After the attack, the targeted organization analyzes the incident, assesses the impact, and implements measures to prevent or mitigate future DDoS attacks.
Mitigating DDoS attacks requires a combination of proactive measures, such as implementing robust network security practices, using DDoS mitigation services, and maintaining situational awareness to respond effectively when an attack occurs.