The history of the Linux operating system is a fascinating journey from a personal project by a student to a global, open-source powerhouse. Here’s an…
What is Operating System ? An operating system (OS) is software that manages the hardware and software resources of a computer system, providing a foundation…
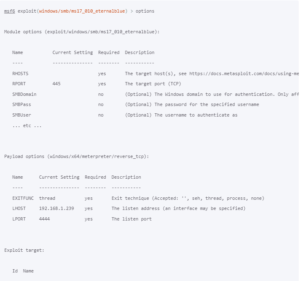
What is Metasploit Framework? The Metasploit Framework is a powerful open-source tool used by cybersecurity professionals and ethical hackers to conduct penetration testing, identify security…
Remote access in ethical hacking refers to the methods and tools used by penetration testers (ethical hackers) to access systems and networks remotely to identify…
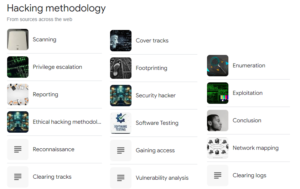
The methodology followed by hackers, particularly those involved in malicious activities, typically involves a series of systematic steps designed to breach security defenses, exploit vulnerabilities,…
Hacktivism is a form of activism that leverages hacking techniques to promote political, social, or ideological agendas. It combines “hacking” and “activism,” reflecting the use…
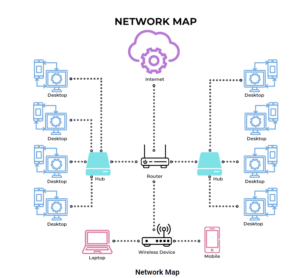
Network mapping can be done using a combination of manual methods and automated tools. Here’s a step-by-step guide to performing network mapping: 1. Define Your…
Keyword search intent (also known as user intent or search intent) refers to the purpose or goal behind a user’s search query. Understanding search intent…
Keyword research is a fundamental part of SEO, helping you identify the search terms that your target audience uses to find information, products, or services.…
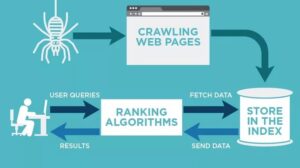
In the context of SEO (Search Engine Optimization), ranking refers to the position of a webpage in the search engine results pages (SERPs) for a…
Google’s crawler, commonly known as Googlebot, sees and interprets web pages differently from how a human user does. It primarily processes the underlying HTML code…
Web crawling tools, also known as web scrapers or spiders, are software applications designed to systematically browse the web to extract and index data from…
Crawling in SEO refers to the process by which search engine bots (also known as spiders or crawlers) systematically browse the web to discover and…
Search Engine Optimization (SEO) is the practice of enhancing a website or online content to improve its visibility and ranking on search engine results pages…
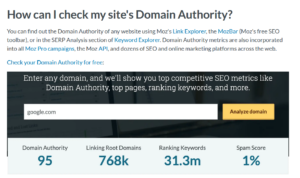
You can check your site’s Domain Authority (DA) using several online tools provided by SEO platforms. Here are some of the most popular options: Moz:…
Domain Authority (DA) is a metric developed by the SEO software company Moz that predicts how well a website will rank on search engine result…
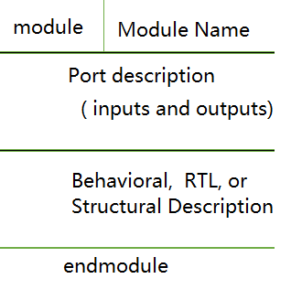
Verilog and Verilog HDL (Hardware Description Language) are essentially the same thing. Verilog is a hardware description language used in electronic design automation, and “HDL”…
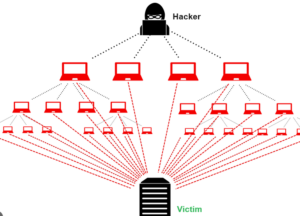
Mitigating a Distributed Denial of Service (DDoS) attack involves implementing various strategies and deploying specialized tools to minimize the impact and restore normal operation. The…
a bandwidth attack aims to overwhelm a network by saturating it with an excessive amount of data, causing the available bandwidth to be fully utilized…
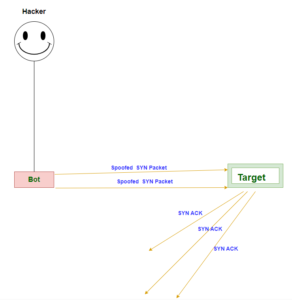
A Distributed Denial of Service (DDoS) attack is a malicious attempt to disrupt the regular functioning of a network, service, or website by overwhelming it…